O - S a f t — OWASP SSL advanced forensic tool
o-saft.pl is an easy to use command line tool to show
informations about SSL certificate and to check the SSL/TLS connection according
given list of ciphers and various SSL/TLS configurations.
In a Nutshell
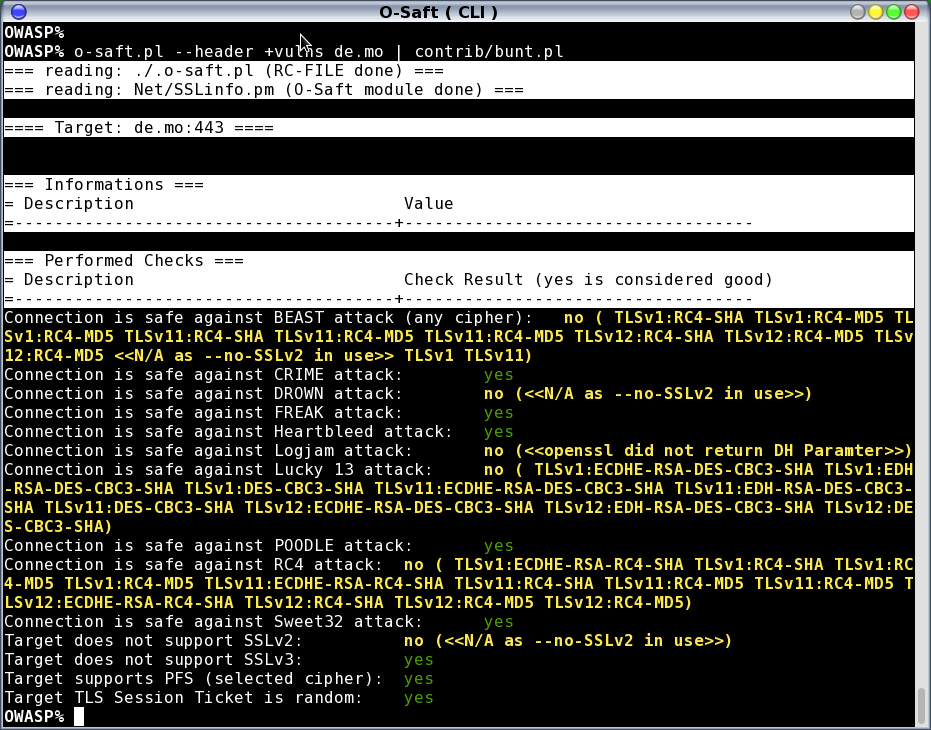
- show SSL/TLS connection details
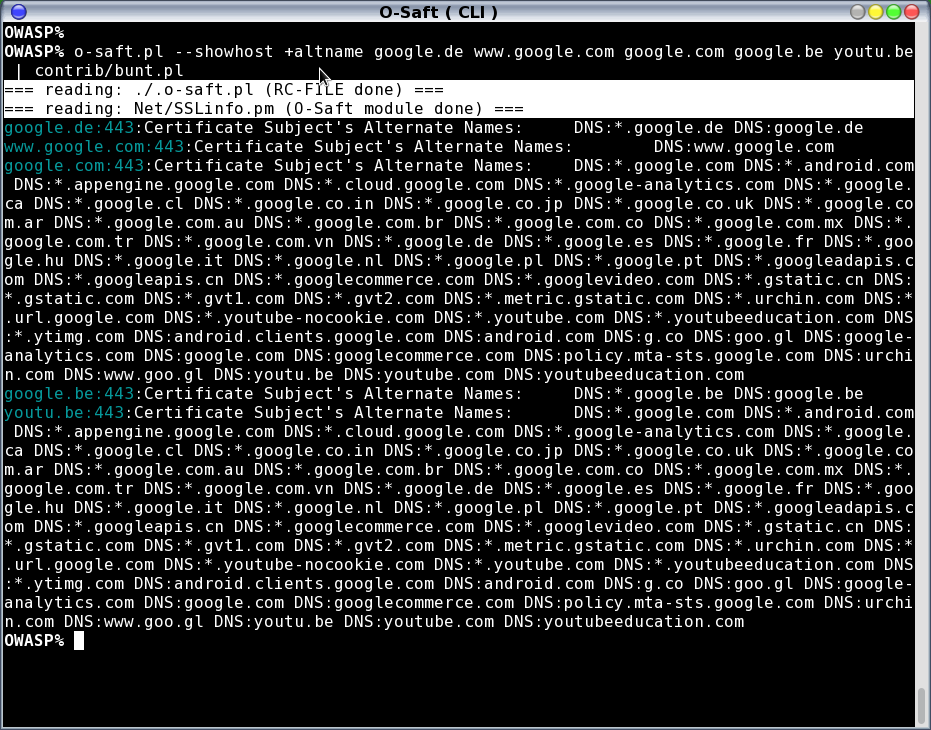
- show certificate details
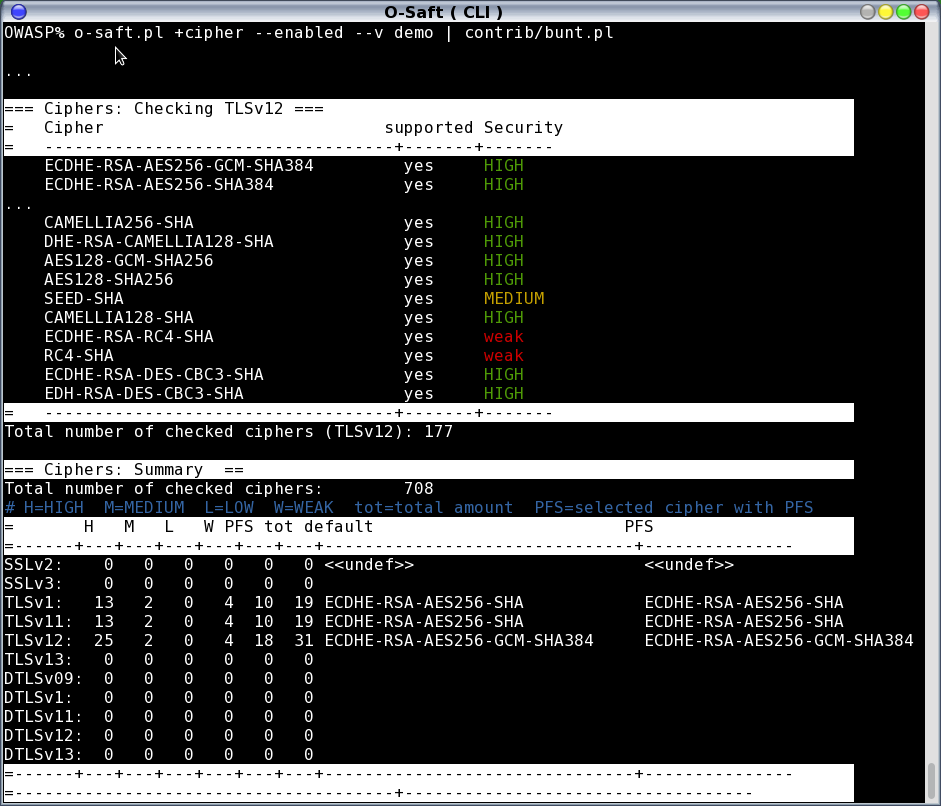
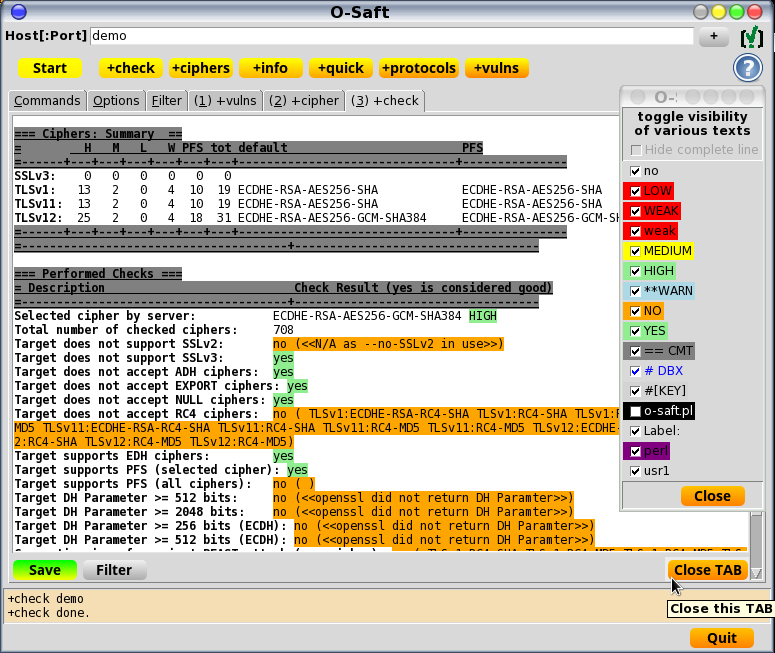
- check for supported ciphers
- should work on any platform (just needs perl; openssl is optional; no CPAN, gems, pip, etc.)
- check for ciphers without any dependency to a library
- may check for ciphers provided in your own libssl.so and libcrypt.so (using openssl)
- check for special HTTP(S) support (like SNI, HSTS, certificate pinning)
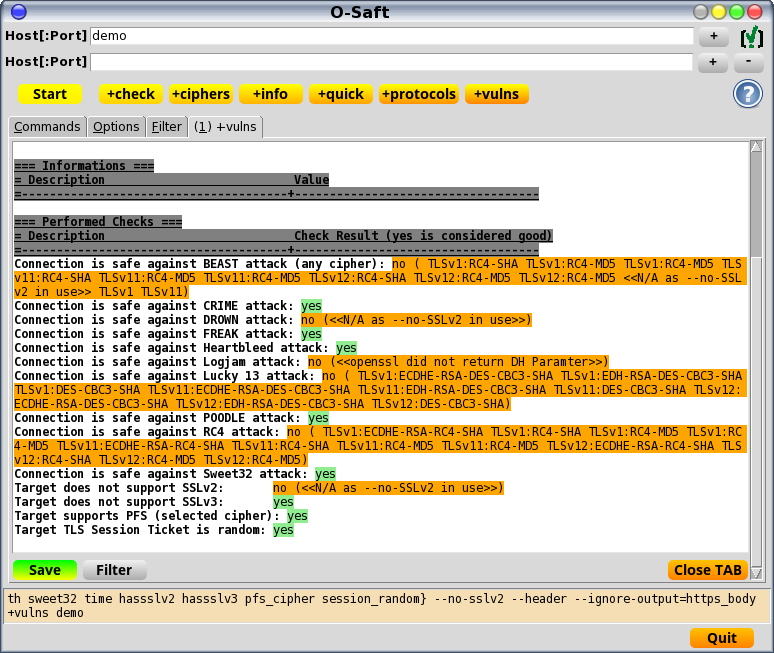
- check for protections against attacks (BEAST, CRIME, DROWN, FREAK, Heartbleed, Lucky 13, POODLE, RC4 Bias, Sweet32 ...)
Advanced features
- checks the server's priority for ciphers
- check the length of Diffie-Hellman parameters by the cipher (checkAllCiphers.pl)
- may check for a single attribute
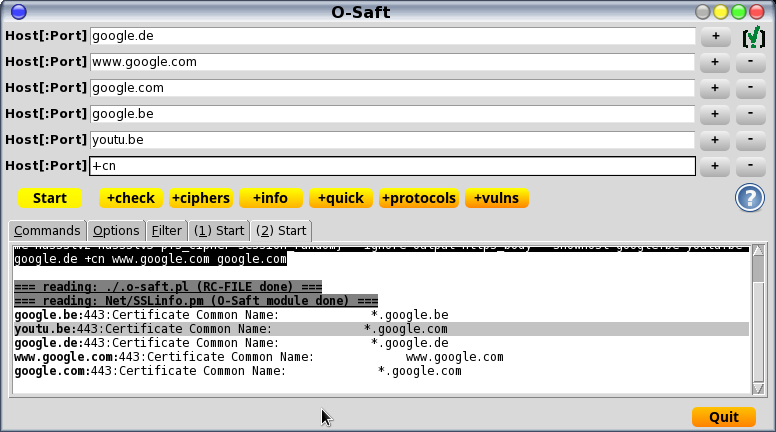
- may check multiple targets at once
- can be scripted (headless or as CGI)
- docker image (usage variants see here)
- output format can be customized (see scripts in usr/ directory)
- various trace and debug options to hunt unusual connection problems
- supports STARTTLS for various protocols like (SMTP, POP3, IMAP, LDAP, RDP,
XMPP, IRC, ...) [without options using openssl]
- supports proxies (besides commands using openssl)
- check of STARTTLS/SMTP for all servers of a MX resource record
- experimental support of DTLS (checkAllCiphers.pl)
Usage
- simple command line script (complete help see here,
more documentation are availabale in doc/ directory)
- as CGI (see example here)
- with GUI
Resources